Path sanitization bypass leading to arbitrary read
February 23, 2024

Products Impacted
This vulnerability is present in ONNX v1.4.0 up to and including v1.15.0.
CVSS Score: 5.5
AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N
CWE Categorization
CWE-22: Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’)
Details
The vulnerability exists within the onnx/external_data_helper.py file, in the load_external_data_for_tensor function. This is triggered when the onnx.external_data_helper._get_all_tensors function is called on a loaded model.
def load_external_data_for_tensor(tensor: TensorProto, base_dir: str) -> None:
"""
Loads data from an external file for tensor.
Ideally TensorProto should not hold any raw data but if it does it will be ignored.
Arguments:
tensor: a TensorProto object.
base_dir: directory that contains the external data.
"""
info = ExternalDataInfo(tensor)
file_location = _sanitize_path(info.location)
external_data_file_path = os.path.join(base_dir, file_location)
with open(external_data_file_path, "rb") as data_file:
if info.offset:
data_file.seek(info.offset)
if info.length:
tensor.raw_data = data_file.read(info.length)
else:
tensor.raw_data = data_file.read()An attacker can exploit this vulnerability by creating an ONNX model with external tensors which contain malicious paths meant to traverse out of the designated directory. However, as can be seen in the above code snippet, there is an attempt to sanitize the path information provided by the user. This is a result of CVE-2022-25882, the predecessor of this vulnerability, which resulted in the developers implementing a sanitization function to prevent path traversals in the external tensor loader.
def _sanitize_path(path: str) -> str:
"""Remove path components which would allow traversing up a directory tree from a base path.
Note: This method is currently very basic and should be expanded.
"""
return path.lstrip("/.")The original patch fixed a large number of path traversals by removing the “/” and “.” characters from the start of a path in order to remove absolute and relative paths being used by an attacker. However, nested path traversal attacks and absolute paths on Windows were not prevented. An attacker could exploit a nested path traversal attack by first going into a directory and then using relative paths to escape it, a very probable attack given that an attacker could provide the model with a directory containing external tensors, thus knowing the path of the directory. This style of attack is not stopped by the above due to the sanitization only stripping the bad characters at the start of a path.
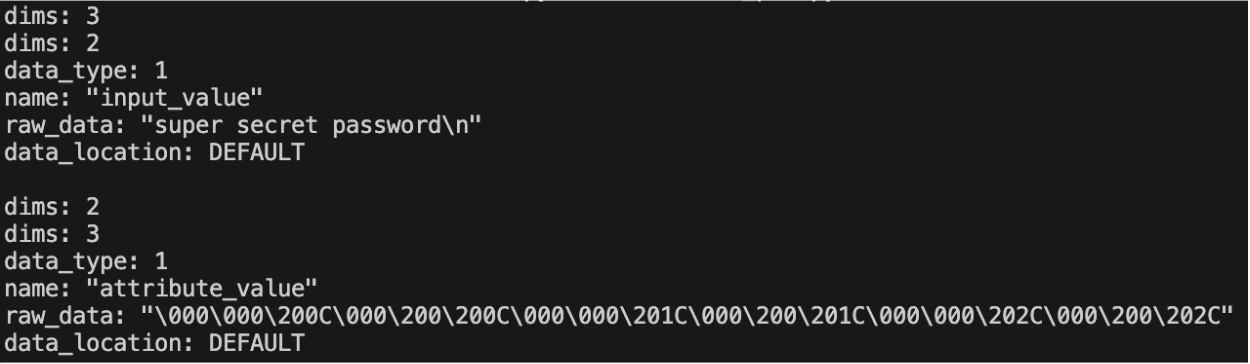
When the user loads a malicious model with an external tensor pointing at external_data/../../secret their system would then load the data from that file into the model:
import onnx
model = onnx.load("model.onnx")
tensors = onnx.external_data_helper._get_all_tensors(model)
for tensor in tensors:
print(tensor)Once run we can see that the super secret password was read.
Related SAI Security Advisory
November 26, 2025
Allowlist Bypass in Run Terminal Tool Allows Arbitrary Code Execution During Autorun Mode
When in autorun mode with the secure ‘Follow Allowlist’ setting, Cursor checks commands sent to run in the terminal by the agent to see if a command has been specifically allowed. The function that checks the command has a bypass to its logic, allowing an attacker to craft a command that will execute non-whitelisted commands.
October 17, 2025
Data Exfiltration from Tool-Assisted Setup
Windsurf’s automated tools can execute instructions contained within project files without asking for user permission. This means an attacker can hide instructions within a project file to read and extract sensitive data from project files (such as a .env file) and insert it into web requests for the purposes of exfiltration.