Crafted WiFI network name (SSID) leads to arbitrary command injection
July 19, 2024

Products Impacted
This vulnerability is present in Wyze Cam V4 firmware versions up to and including 4.52.4.9887.
CVSS Score: 6.8
AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-78: Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’)
Details
This vulnerability is caused by the net_service_thread function in the /system/lib/libwyzeUtilsPlatform.so library.
00004604 snprintf(&str, 0x3fb, "iwlist wlan0 scan | grep \'ESSID:\"%s\"\'", 0x18054, var_938, var_934, var_930, err_21, var_928);
00004618 int32_t $v0_6 = exec_shell_sync(&str, &var_918);The net_service_thread function is used by the init_net_service function which is invoked by /system/bin/iCamera during the camera setup process. The purpose of this function is to initialize the camera’s wireless networking.
The user-specified WiFi network name (SSID) provided during the camera setup is passed to a shell command without sanitization. An attacker within Bluetooth range of the camera can exploit this by specifying a network name containing a command enclosed in single quotes followed by a semicolon.
To replicate this vulnerability, the Wyze app can send the camera a crafted WiFi network name containing the command to execute.
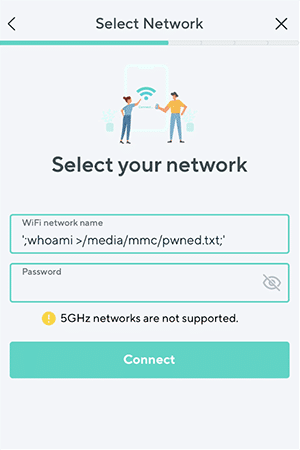
After hitting the Connect button, the command will be sent to the camera over Bluetooth and executed through the exec_shell_exec function. In the example pictured above, the command whoami is executed, and the output is piped to a file named pwned.txt on the root of the camera’s SD card.
The command injection is saved to the camera’s config and persists across reboots. During our testing, we found that it was possible to brick the camera by providing it with a WiFi network name containing the reboot command.
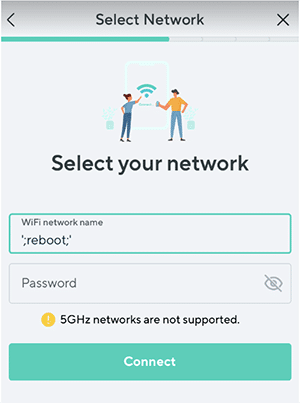
This resulted in the camera going into an endless reboot loop that we could not exit.
Related SAI Security Advisory
November 26, 2025
Allowlist Bypass in Run Terminal Tool Allows Arbitrary Code Execution During Autorun Mode
When in autorun mode with the secure ‘Follow Allowlist’ setting, Cursor checks commands sent to run in the terminal by the agent to see if a command has been specifically allowed. The function that checks the command has a bypass to its logic, allowing an attacker to craft a command that will execute non-whitelisted commands.
October 17, 2025
Data Exfiltration from Tool-Assisted Setup
Windsurf’s automated tools can execute instructions contained within project files without asking for user permission. This means an attacker can hide instructions within a project file to read and extract sensitive data from project files (such as a .env file) and insert it into web requests for the purposes of exfiltration.